By Vivek Acharya – BIG United States Ambassador
This blog is little different from my usual contents on Oracle Products. In this article, we will give an overview of Ethereum wallets as well as their types. We start by explaining what wallet technology is, its role in blockchain applications and how it works. Then, we explain two major types of wallets: deterministic and non-deterministic wallets.
Due to the popularity of blockchain and decentralized finance, many applications that offer digital currencies like Bitcoin or Cryptocurrencies, come with a feature called digital wallet. A wallet allows users to store and manage their private keys. A wallet is also used for key generation. Depending on the platform in which a user can access and manage their wallet, there are 4 types of wallets: web, desktop, mobile, and Hardware.
Another way to categorize wallets is based on the way in which keys are generated which includes deterministic and non-deterministic wallets. A non-deterministic wallet is considered a rather old style compared to a deterministic wallet. Modern deterministic wallets have advantages over non-deterministic wallets in many aspects, such as backups, security, data storage, accounting, auditing, and access controls.
Understanding the wallet technology
When we refer to something as a wallet, we assume that it’s something that holds money. In fact, an Ethereum wallet does not store any ether or tokens. Wallets keep the private keys that are needed for signing the transactions. An Ethereum wallet, just like a cryptocurrency wallet, can be classified as a non-deterministic or deterministic wallet.
Understanding non-deterministic and deterministic wallets
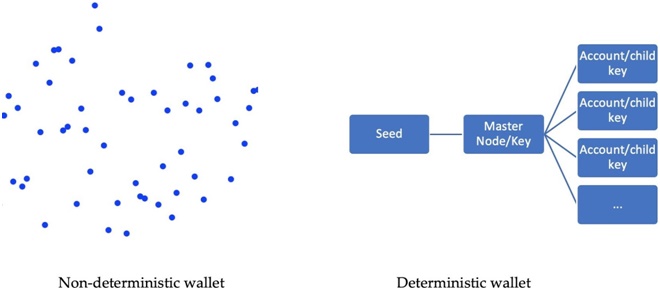
What’s the difference between these two types of wallets? They are different in how the private keys are backed up. A non-deterministic wallet generates private keys that are random and independent of each other (such as in the left-hand side of the following diagram). There is no particular pattern as to how the keys are derived and hence we need to create a backup of the keys each time there is a new one. In a deterministic wallet, on the contrary, the private keys are related because they originate from the same key called seed, as shown here on the right-hand side of the diagram. Just backing up the seed once will be enough to regenerate all the keys:
There are three types of deterministic wallets:
- Deterministic wallet
- Hierarchical Deterministic (HD) wallet
- Armory deterministic wallet
The first wallet, which is used in Ethereum presale, is a non-deterministic wallet. It’s considered a rather old style compared to a deterministic wallet. Modern deterministic wallets have advantages over non-deterministic wallets in many aspects, such as backups, security, data storage, accounting, auditing, and access controls. The following list showcases some of these advantages:
- One-time backup for deterministic wallets is so much easier than the cumbersome way a non-deterministic wallet has to be backed up. If you don’t create a backup each time, you will risk losing the data, which is referring to ether and smart contracts. For a deterministic wallet, only copying the master seed will be enough. It’s less work during the import and export of wallets. For a non-deterministic wallet, the entire list of keys needs to be copied during the migration process.
- In the concept of deterministic wallets, deriving the keys from the seed makes it possible to store the private keys offline. Disabling web server access to private keys offers more privacy and security. Securing the seed takes less effort compared to keeping all the keys safe, which is what non-deterministic wallets need to do.
The HD wallet is the most well-known kind of deterministic wallet. It’s also a preferred option among the deterministic wallets if you want to create one since it is well developed. When it comes to the following cases, the HD wallet shows more advantages than other types of deterministic wallet:
- Use cases for creating public keys without accessing corresponding private keys
- Use cases for keys to match the hierarchical structure in an organization context
The first use case shows the security advantage of the HD wallet. Normally, a deterministic wallet holds a single chain of keypairs, which doesn’t support selective keypair sharing, while the HD wallet allows such selective sharing on multiple keypair chains that are generated from a single root. In some cases, being able to create public keys without exposing private keys makes the HD wallet available in environments that would normally be a higher security risk. The second use case listed here takes advantage of the hierarchical structure of the design and puts it into the use of real-world cases.
HD wallet has security advantages just mentioned previously, we will bring up another aspect of secure consideration—private key management. It does not only refer to key generation offline (away from the network, such as cold storage. Key sharding and splitting or division of signatures are other alternatives. Key sharding, also known as Shamir’s secret sharing, is basically splitting a key into several pieces, or shards. This makes each shard useless, and the original key would be reconstructed unless enough pieces are assembled to reconstruct. A similar but very different concept to this is multi-signature wallet. Readers who are interested in the topic are encouraged to do further reading about this.
With cryptocurrency wallets becoming more and more developed, the protocols and standards need to be shared across the industry. The Ethereum community has been establishing standards over the years. Some of them are known as Ethereum Improvement Proposals (EIPs). Some are on application-level standards, for example, the standard format for smart contracts, known as Ethereum Requests for Comment (ERC). Standards are also followed for wallet creation. There are a few standards that are widely adopted, as follows:
- HD wallets (BIP-32)
- Multipurpose HD wallets (BIP-43)
- Multi-currency and multi-account wallets (BIP-44)
- Mnemonic code words (BIP-39)
BIP stands for Bitcoin Improvement Proposal. Although there are so many differences between Bitcoin and Ethereum networks today, they still have a lot in common and share standards and protocols.
The mnemonic code words is 128-bit to 256-bit entropy. This entropy will be plugged into a Password-Based Key Derivation Function 2 (PBKDF2) function and stretched to a 512-bit seed. The seed will be used in building a deterministic wallet. In our next article, we will review HD wallet or BIP- standard in depth.
Summary
In this article, we learn about wallet technology and its role in blockchain. We also discuss different types of Ethereum wallets: deterministic and non-deterministics. In our next article, we will explain one of the most popular Ethereum wallet categories or Hardware wallet (that is based on BIP- standard).
Resources
Here is a list of resources for learning more about blockchain development with Ethereum:
- Hands-on Smart Contract Development with Hyperledger Fabric
- Oracle-Blockchain-Services Quick Start Guide
This article is written in collaboration with Matt Zand who is the founder of: DC Web Makers, Hash Flow, Coding Bootcamps and High School Technology Services. He is also the leading author of Hands-on Smart Contract Development with Hyperledger Fabric book by O’Reilly Media.



